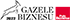.
Cybersecurity of critical infrastructure – the water and sewage sector in relation to NIS2
Just a few years ago, cyber threats to the water and sewage sector seemed distant and theoretical. Today, they are a brutal reality. Reports of another attack on a water treatment plant in Poland show that the infrastructure responsible for providing basic services to citizens has become the focus of cybercriminals.
Some of the cyber attacks have been confirmed by the CERT Polska team, which operates within the structures of NASK – the National Research Institute. Details can be found in the article on the website:
Recommendations for strengthening the protection of OT systems | CERT Polska
Find out:
-
The growing wave of cyber attacks on critical infrastructure
-
NIS2 – the foundation of a new approach to security
-
Why is the water and sewage sector so vulnerable?
-
Find out what distinguishes operational technologies (OT) from information technologies?
-
Examples of OT applications – from factories to developed networks
Rosnąca fala cyberataków na infrastrukturę krytyczną
The growing wave of cyberattacks on critical infrastructure
Just a few years ago, cyber threats to the water and sewage sector seemed distant and theoretical. Today, they are a brutal reality. Reports of another attack on a water treatment plant in Poland show that the infrastructure responsible for providing basic services to citizens has become the focus of cybercriminals.
The problem is not limited to Poland. In the United States, there was widespread coverage of an alleged attack on the water supply control system in Florida, where, according to reports, hackers attempted to raise the level of harmful substances in the water. Although the information on this case remains unclear, it is worth paying attention to the problem itself and drawing conclusions from it. There have also been cases of attempted interference with energy and water management systems in Europe. The trend is clear – attacks are increasingly targeting critical infrastructure, as striking it has the greatest destabilising effect.
Water supply systems are inherently distributed and rely on numerous telemetry devices. They often connect multiple stations , pumping stations, sensors and control systems. Each of these elements becomes a potential entry point for an attacker. If cybercriminals gain access to such a system, they can not only interrupt the water supply, but also attempt to manipulate its quality – and this poses a direct threat to human health and life.

NIS2 – the foundation of a new approach to security
The European Union has responded to the growing threats by adopting the NIS2 Directive, which came into force in October 2024. The new regulations significantly expand the list of sectors and entities required to ensure a high level of cybersecurity.
They include, among others:
- energy,
- transport,
- healthcare,
- public administration
- and the water and sewage sector.
What does this mean in practice? The Directive imposes an obligation on entities to implement a number of mechanisms:
- monitoring and reporting incidents to national authorities and CERTs,
- risk management through regular audits and vulnerability analyses
- implementation of encryption of communication
- operational resilience, i.e. the ability to maintain system operation even in the event of an attack.
NIS2 also changes the responsibilities of managers. The management of companies and institutions should be aware of their responsibility to implement security measures. This enforces a new culture of IT and OT management.
IT (Information Technology) – all computer systems and networks used for data processing: computers, servers, office software, e-mails, databases, ERP systems. In short, the world of digital information in a company.
OT (Operational Technology) – operational technology, systems and devices that control physical processes: PLC controllers, SCADA, sensors, production lines, industrial equipment, water treatment plants and power grids. In short, the world of machines and industrial automation.
Why is the water and sewage sector so vulnerable?
Water supply systems are largely based on equipment and software developed many years ago, which were not designed with today’s cyber threats in mind. Many installations still use unsecured communication protocols, and updates are rarely implemented, mainly due to concerns about service interruptions. As a result, security issues often take a back seat to the daily responsibilities of technical teams.
In practice, this means that a potential attacker does not need to have advanced skills – all they need to do is exploit weak passwords, lack of transmission encryption or vulnerable software. For this reason, the water and sewage sector today requires special attention and support in terms of modernising OT systems and improving cybersecurity.
Why is the water and sewage sector so vulnerable?
Water supply systems are largely based on equipment and software developed many years ago, which were not designed with today’s cyber threats in mind. Many installations still use unsecured communication protocols, and updates are rarely implemented, mainly due to concerns about service interruptions. As a result, security issues often take a back seat to the daily responsibilities of technical teams.
In practice, this means that a potential attacker does not need to have advanced skills – all they need to do is exploit weak passwords, lack of transmission encryption or vulnerable software. For this reason, the water and sewage sector today requires special attention and support in terms of modernising OT systems and improving cybersecurity.
Find out what distinguishes operational technologies (OT) from information technologies
Key features of OT systems:
- they are used to control machines and physical processes (e.g. in factories, energy, transport, waterworks),
- they include both devices (sensors, PLC controllers, robots, SCADA, DCS) and software that manages their operation,
- their priority is process continuity and security – more than data confidentiality (unlike traditional IT systems),
- they are increasingly connected to IT systems (e.g. the cloud, ERP), which increases efficiency but also exposes them to cyber threats.
Discover examples of OT applications – from factories to advanced networks
Examples of OT applications:
- SCADA systems in water supply and sewage systems,
- industrial automation in manufacturing plants,
- power grid control (Smart Grid),
- railway and air traffic management,
- robotics in logistics and warehouses.

Attacks on critical infrastructure are not a thing of the future – they are happening now. Due to its social importance, the water and sewage sector has become a natural target for cybercriminals. The NIS2 Directive requires entities to take real action in the area of cybersecurity. For many entities, this means investing in modern solutions and changing their approach to IT and OT infrastructure management.
The challenge is enormous, but what is at stake is the safety of citizens and the economy (continuity of water supply). Responsible implementation of new standards and the use of proven technologies is the only way to effectively meet the demands of the digital reality.
Start now
Read more articles:

Cybersecurity – no catches or hidden costs. What are we implementing today?
Find out what real changes we are implementing today to secure critical infrastructure.

AGREUS® – effective support for modern agriculture
Support for modern agriculture – monitor crops, control the system and increase efficiency